HackTheBox Starting Point Tier 1 machine: Crocodile walkthrough
Complete walkthrough with answers for the HackTheBox starting point tier 1 machine: Crocodile
Table of contents
🔧Setup
First, we need to connect to the HTB network. There are two different methods to do the same:
- Using Pwnbox
- Using OpenVPN
(Click here to learn to connect to HackTheBox VPN)
🌟Introduction
Sometimes people may leave FTP service misconfigured or with default credentials or with anonymous login turned on, in this machine we are going to exploit an FTP service that allows anonymous logins and using that we are going to break into the administrative panel of a webpage! Let’s start
🔍Scanning and enumeration
You can refer to this write-up for the starting steps (eg: spawning machine, checking connection using ping)
Now let's start scanning the target using nmap to find any open ports and services
We can use the following nmap command: sudo nmap -sC -sV {target_ip}
{target_ip} has to be replaced with the IP address of the machine.
The -sC switch is used to perform script scan using default set of scripts. The -sV switch is used to display the version of the services running on the open ports.
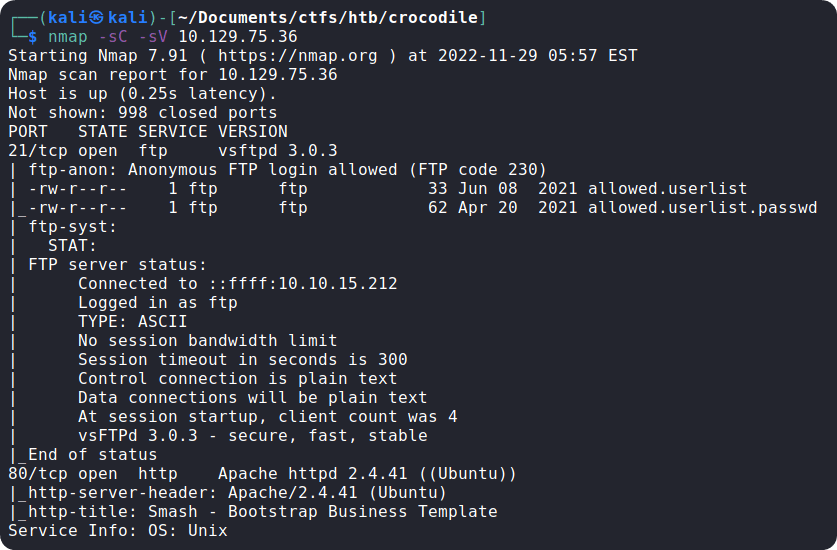
From the nmap scan we can see that ports 21 (FTP) and 80 (HTTP) are open, and FTP server is configured to allow anonymous login, i.e., we can login to the FTP server even if we have no valid credentials.
Now we can try to connect to the FTP server using the command, ftp {target_ip}
We will pass in anonymous as the username and leave the password field blank (since it allows anonymous logins)
After logging in we can use the help command to see all the possible commands we can execute on the server
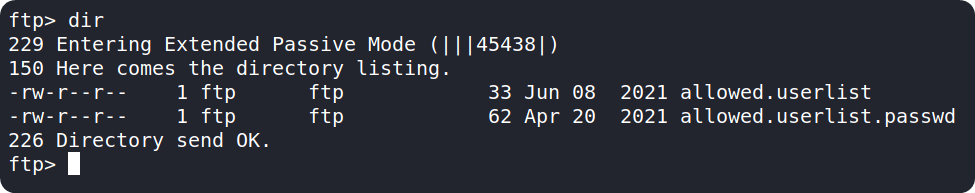
We can use the dir command to list the contents of our current directory. Upon executing the command, we can see there are two files in the directory which might be useful for us.
We can use the get command followed by a filename to download both files to our local machine.
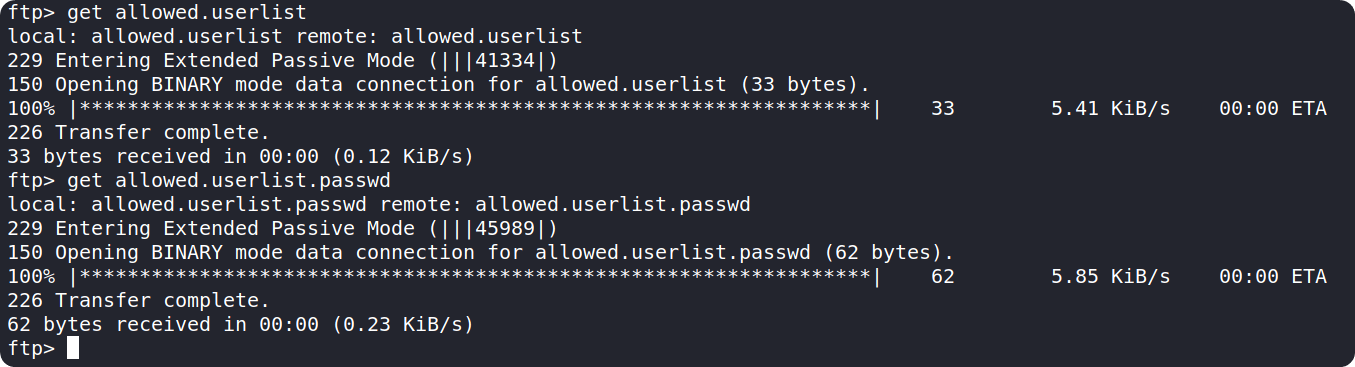
After downloading, we can terminate the FTP connection by typing in exit command
Using ls in the current working directory of local machine will show us the files which we just download from the ftp server. We can use cat command to see the contents of both the files.
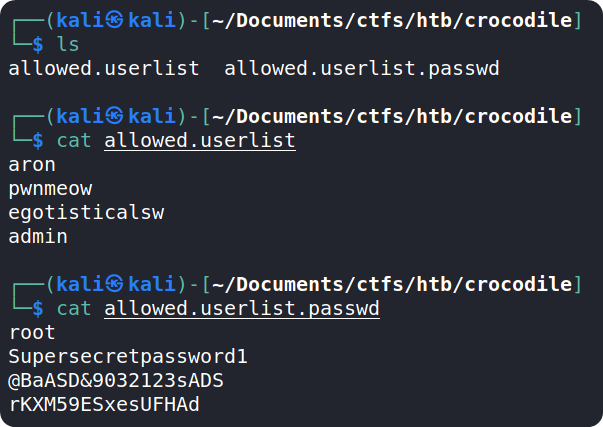
We can see that the files contain the usernames and the passwords associated with those usernames
🐾Foothold
While trying to login to the ftp server using the obtained credentials, we get an error. So, we can now try to use these credentials on the web server running on port 80 which we found during our nmap scan.
When we type the IP address of the machine into the browser and press enter, we get a web page like this:
We can use a browser extension called Wappalyzer to identify the technologies used in this website
After installation, we can press the wappalyzer icon on the browser to reveal the tech stack using in our target website
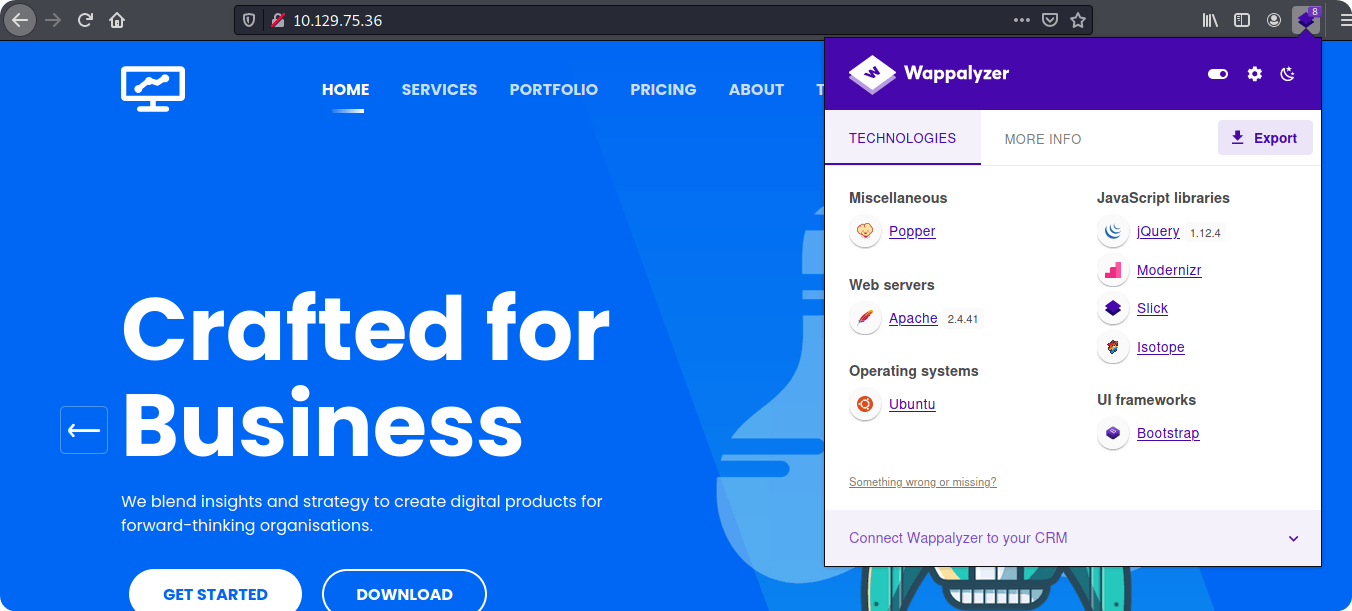
We can see that the website is using PHP as its programming language.
Now, we can search for different directories and pages within the website, but doing so manually is time-consuming. Lucky, we have tools for it, one such tool is gobuster
We can use the below command to search for directories and html or php pages within the website:
gobuster dir -u http://{target_ip}/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -x php,html
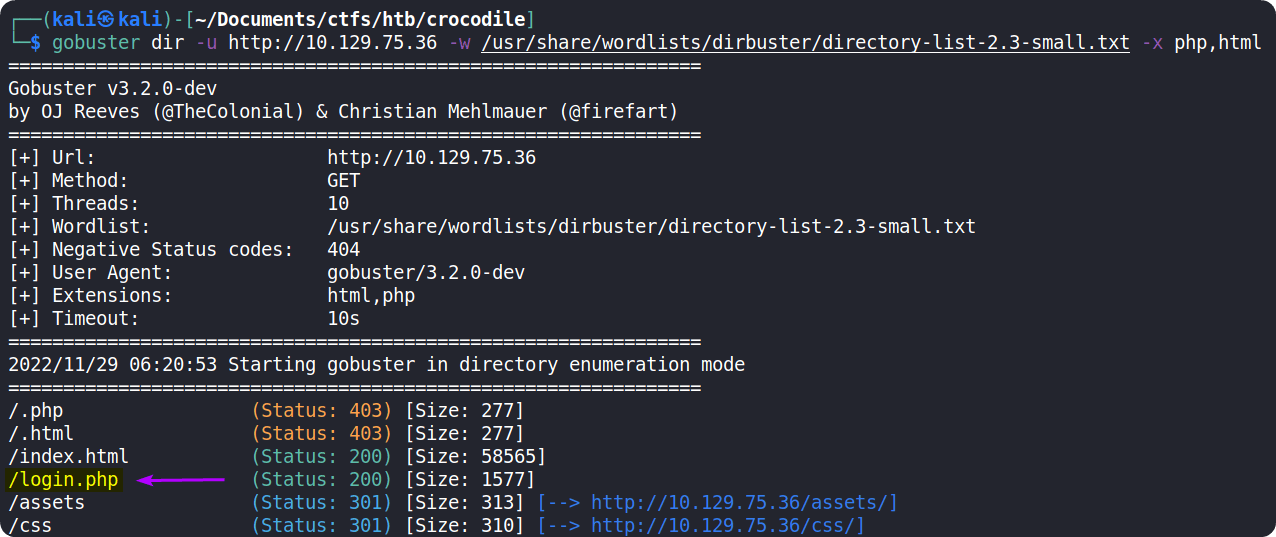
We can see that gobuster found a page called /login.php.
Visiting this page in the browser, we can see a login form:
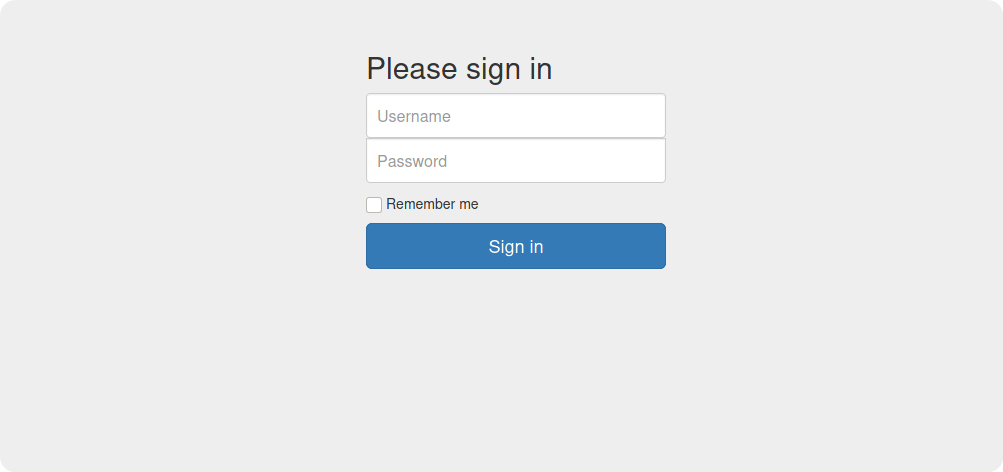
We can try the credentials which we got before, in this page. You can either do it manually or use Burp Suite. After trying some of the usernames and passwords, we have successfully logged into the admin panel
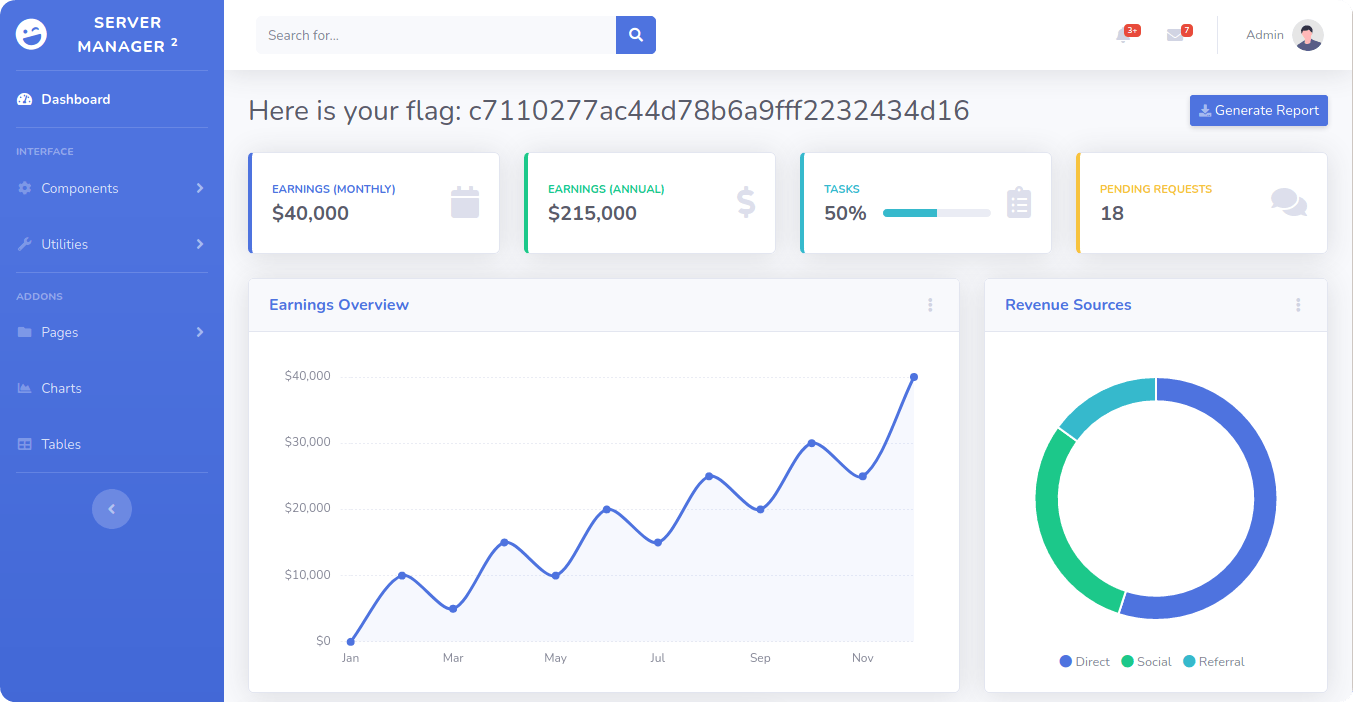
Copy the flag value and paste it into the Starting Point lab's page to complete your task.
Congrats, you have just pwned Crocodile! 👏
✔️Task answers
Task 1: What nmap scanning switch employs the use of default scripts during a scan?
-sC
Task 2: What service version is found to be running on port 21?
vsftpd 3.0.3
Task 3: What FTP code is returned to us for the "Anonymous FTP login allowed" message?
230
Task 4: What command can we use to download the files we find on the FTP server?
get
Task 5: What is one of the higher-privilege sounding usernames in the list we retrieved?
admin
Task 6: What version of Apache HTTP Server is running on the target host?
2.4.41
Task 7: What is the name of a handy web site analysis plug-in we can install in our browser?
Wappalyzer
Task 8: What switch can we use with gobuster to specify we are looking for specific filetypes?
-x
Task 9: What file have we found that can provide us a foothold on the target?
login.php
🚩 Root flag:
c7110277ac44d78b6a9fff2232434d16
🌐 Connect with me: tenocijam.in